In the fast-evolving landscape of software development, tech teams are constantly challenged to innovate, scale, and deliver products that not only meet but exceed market demands and expectations. The Build-Operate-Transfer (BOT) model has emerged as a leading approach, offering a strategic framework for businesses to enhance their digital capabilities. In this deep-dive exploration, we will unravel the potential of the BOT model and how it is paving the way for future-proof software solutions in the life sciences industry.
Unveiling the BOT Model
The BOT model, renowned for its flexibility and efficiency, is more than just a project management technique—it is a comprehensive strategy for long-term success in software development. With its ability to provide immediate access to talent, streamline operations, and foster sustained innovation, the BOT model has become a staple for businesses seeking an edge in the digital domain.
But what exactly is the BOT model, and what makes it tick?
The Essence of Build-Operate-Transfer
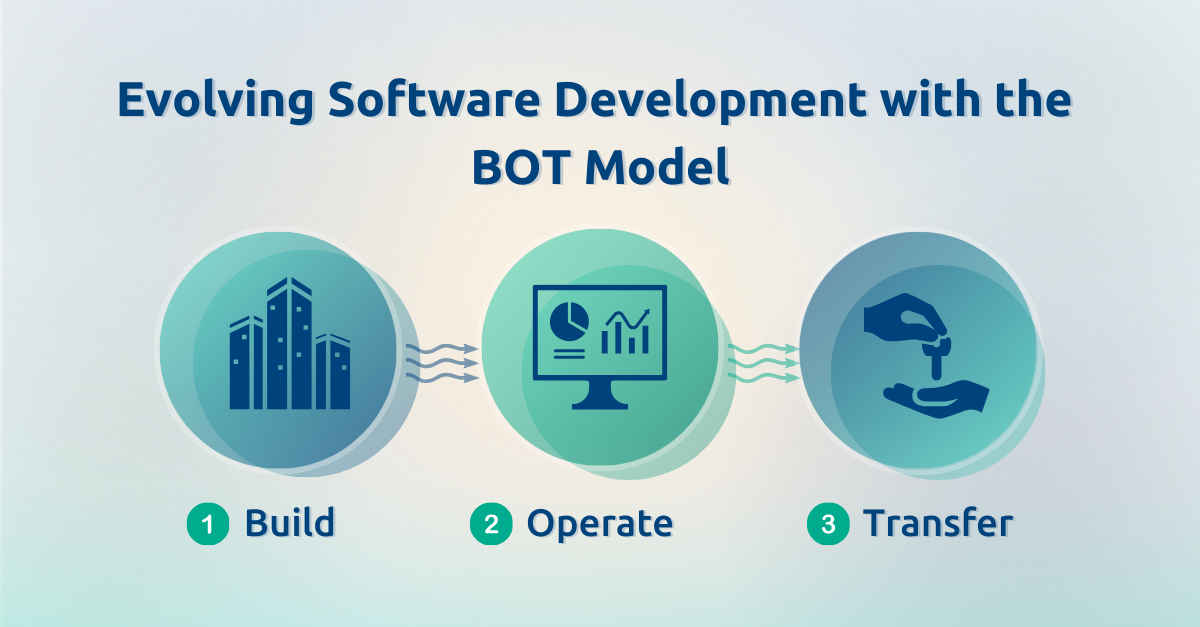
At its core, the BOT model can be defined as a project management approach where a company enters into a partnership with a third-party firm to create a new product or subsidiary. This collaborative method involves three distinct phases:
- Build: The partner company is responsible for the initial construction and development of the project, leveraging its expertise to lay the groundwork for success.
- Operate: Upon completion, the partner company assumes the responsibility of operating the project on a day-to-day basis. This stage is crucial for refining operations, ensuring quality, and leveraging ongoing support for the system to evolve.
- Transfer: The final stage involves the transfer of the fully operational project to the original requester, equipped with the knowledge and capabilities to manage it effectively.
Probing into the Benefits and Challenges of the BOT Model
Few models can rival the BOT approach’s array of benefits, but it is not without its challenges. To truly assess its viability, we must dissect both.
The Benefits of the BOT Model
The BOT model is designed to offer a wealth of advantages, including:
- Cost Savings: By spreading the investment across the entire life cycle of the project, the BOT model can significantly reduce upfront costs and unlock additional capital for critical business activities.
- Access to Expertise: Business partnerships under the BOT model provide access to specialized knowledge, cutting-edge technologies, and innovative approaches that can elevate project outcomes.
- Reduced Time-to-Market: With streamlined operations and continuous improvement mechanisms in place, the BOT model ensures a swifter launch, allowing businesses to capitalize on market opportunities more swiftly.
- Risk Mitigation: The shared responsibility inherent to the BOT model helps distribute and manage risks effectively under the guidance of experienced partners.
- Knowledge Transfer: Through the occupation phase, the partner organization equips the client with operational insights and capabilities to foster autonomy and future success.
Navigating the Challenges
While the BOT model offers compelling advantages, it requires careful planning and execution to overcome potential challenges such as:
- Adapting to New Partnerships
- Balancing Control and Collaboration
- Ensuring Successful Knowledge Transfer
Stacking Up Against Other Software Development Models
How does the BOT model compare to other project management techniques like outsourcing and traditional in-house development? The answer lies in its unique combination of flexibility and strategic partnership. Unlike traditional outsourcing, the BOT model entails direct collaboration with the partner company throughout the life cycle. Conversely, in-house development may lack the cost-effectiveness and sometimes the expertise that the BOT model provides through its partnership’s access to specialized resources.
By fostering a dynamic synergy of build, operate, and transfer phases, the BOT model strikes a balance that resonates with businesses seeking to optimize resources and facilitate sustainable growth.
Delving Deeper: Understanding the Build, Operate, Transfer (BOT) Process
For a software solution’s success story, the BOT model’s operational intricacies are vital. Each phase plays an indispensable role in steering the project toward a future-proof outcome.
Build Phase: Laying the Foundation for Success
In the initial build phase, the aim is to create a strong architectural design and foster an agile, scalable system. This is where partners help in the construction of a project that aligns with industry standards, regulatory frameworks, and the business’s strategic goals.
Operate Phase: Ensuring Smooth Sailing and Continuous Improvement
During the operate phase, the developed solution undergoes rigorous testing and operational refinement under the partner’s management. Continuous monitoring, optimization, and responsive maintenance support the product’s evolution in a dynamic landscape.
Transfer Phase: Steering Towards Independence and Continued Support
The transfer phase is the culmination of the partnership, where the project is handed over to the client with all operational controls and capabilities. This is supported by robust knowledge transfer initiatives that equip the client to seamlessly manage the system.
Success Uncovered: Companies Flourishing with the BOT Model
The real testament to the BOT model’s effectiveness is in its adoption and success stories within the life sciences sector. By highlighting the journeys of companies that have leveraged the BOT model, we gain insights into its tangible impact and potential rewards.
Case Study 1: Nearshore Partnership Catalyzed Groundbreaking Advances in Diabetes Care
The customer, a leading healthcare tech company, faced challenges scaling operations to meet high demand for their diabetes care solution. Establishing a Center of Excellence in Tijuana, Mexico, using ITJ’s BOT model, solved location, talent, culture, and compliance hurdles. This approach drove innovation, matched product growth, and ensured regulatory adherence. Over 20 core products were launched, boosting market position. Product reliability increased above 80%, enhancing customer trust. The Tijuana center expanded to 260+ engineers, elevating capabilities. Success metrics and feedback show efficient scaling, improved quality, and sustained innovation. ITJ’s expertise and cost-effective nearshore model position them as an ideal healthcare software engineering partner. See the full case study here.
Case Study 2: How ITJ’s Client Quadrupled its Product Releases
ITJ’s client, a leading medical device company, faced the challenge of boosting its digital engineering capacity to meet product goals due to a shortage of software engineers in Southern California. Seeking help from ITJ, they utilized the BOT model, adding 260+ engineers from Tijuana rapidly and cost-effectively. This move increased their capabilities tenfold and received positive feedback for providing high-quality talent and overcoming talent scarcity. The BOT model by ITJ effectively addressed the talent shortage issue, aiding the client in expanding their engineering capacity efficiently and achieving market success. See the full case study here.
Forecasting the Future: The BOT Model’s Role in Next-Gen Software Development
Looking ahead, the BOT model continues to be a harbinger of next-generation software development practices. Its unique value proposition is poised to shape tomorrow’s technological landscape within the life sciences domain.
BOT Model: A Catalyst for Technological Excellence in Life Sciences
For companies in the life sciences realm, the BOT model offers more than just a development framework. It serves as a catalyst for technological excellence, allowing for the creation of cutting-edge solutions that advance the industry as a whole.
Digital Excellence, Cost Optimization, and Regulatory Compliance: The BOT Advantage
In an environment fraught with challenges related to regulatory scrutiny and cost pressures, the BOT model emerges as a beacon of hope. Its ability to integrate digital excellence, cost optimization, and regulatory compliance into the fabric of software development sets it apart as a game-changer.
Technology and the BOT Model: Shaping the Future of Life Sciences
The integration of emerging technologies with the BOT model promises an exciting trajectory for the life sciences sector. By harmonizing innovative solutions with a structured approach to development, businesses can unlock the full potential of the BOT model.
Conclusion: Embracing the BOT Model for a Future-Ready Software Development Landscape
The BOT model is not just a passing trend; it is a strategic imperative for companies in the life sciences industry looking to fortify their digital presence. Its principles of collaboration, efficiency, and innovation resonate deeply with the challenges and opportunities of the 21st-century marketplace.
In conclusion, as we stand on the precipice of a new era in software development, the BOT model offers a compelling path to future-proof solutions. By fostering a culture of continuous improvement and partnership, businesses can unlock a world of possibilities—laying the groundwork for sustained digital excellence and growth. For companies in the life sciences segment, the question is no longer ‘if’ but ‘when’ to incorporate the BOT model into their development strategy. The future is here, and it is built, operated, and transferred through the lens of the BOT model.